Project Info
Service
Product Development, Cloud Integration, Security & Compliance Engineering, Human-in-the-Loop System Design
Industry
Artificial Intelligence (AI), Enterprise Software / SaaS, Data Privacy & Compliance (e.g., GDPR)
Summary
We partnered with an EU-based AI start-up to deliver a cloud-native, GDPR-compliant meeting intelligence platform that transforms voice data into structured outputs such as summaries and transcripts. The system was designed from the ground up with strong security and data protection principles, enabling secure and efficient processing of audio data while supporting cost-efficient scalability. To validate our implementation, a leading independent security firm conducted a comprehensive penetration test across application, API, and cloud infrastructure layers.
Note: Some architectural and implementation details have been intentionally generalised or omitted due to security and confidentiality considerations.
Project Goals
- Build secure foundations aligned with GDPR and enterprise security expectations
- Design encrypted boundaries and strong identity controls from day one
- Enable safe handling of sensitive user-generated voice content
- Pass an independent third-party penetration test before enterprise onboarding
- Maintain strong security posture without relying on expensive vendor tooling
Key Problems
- Processing large-scale voice data and converting it into structured, user-linked information
- Protecting sensitive content under strict European privacy regulations
- Securing APIs used for transcription and content analysis workflows
- Ensuring data and access separation between different customer teams
Our Approach
From the start, the system followed a "Secure by Design, Efficient by Default" approach:
- Leveraged open-source components and built-in cloud-native controls
- Applied encryption across service boundaries
- Practised least-privilege access and secure defaults
- Included threat modelling during the architecture phase
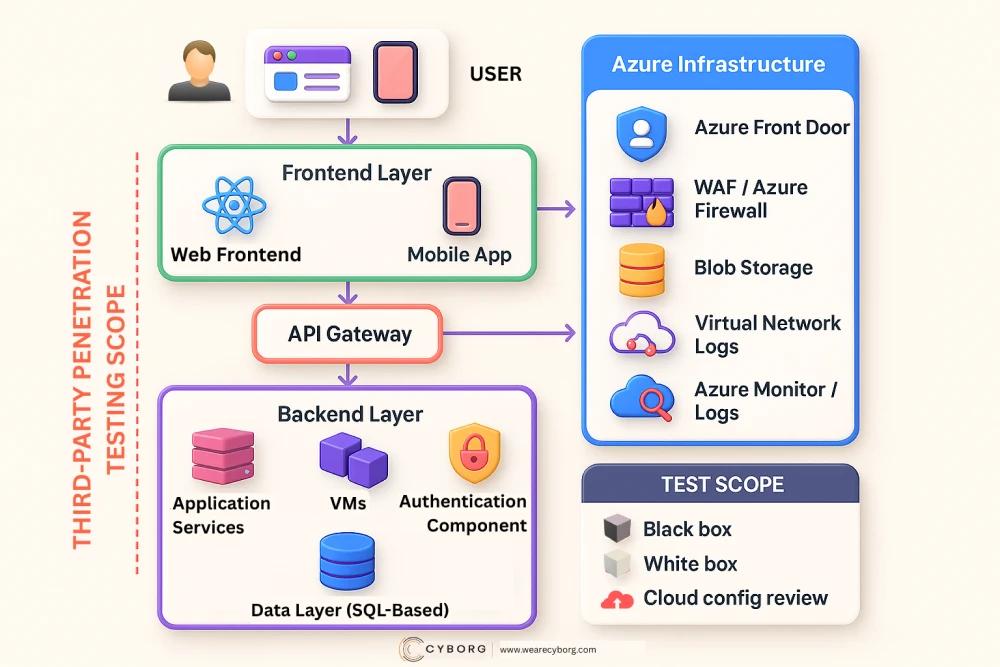
The infrastructure was built using Azure Virtual Machines, Function Apps, managed Postgres databases, and Azure Storage, integrated via secure cloud-native patterns. Front-ends were implemented using web and mobile clients.
Independent Penetration Testing
A third-party security firm conducted a comprehensive assessment, which included:
- Black Box Testing – external attack simulations without prior code access
- White Box Testing – in-depth code and configuration review
- Azure Configuration Review – validation of infrastructure setup against best practices
Testing Scope
- Web and mobile front-ends
- Azure Blob Storage
- Backend APIs developed using a combination of open technologies, including Node.js and Python, exposed securely via Azure API Gateway
- AI pipeline components
- Azure infrastructure components including VMs, Function Apps, Web Apps, managed databases, Azure Storage, and network resources
Activities Included
- Vulnerability testing based on OWASP Top 10:
- Broken Access Control
- Cryptographic Failures
- Injection, Insecure Design, Security Misconfiguration
- Vulnerable Components, Identification Failures, SSRF, and others
- Attempted escalation to system, database, or OS access
- Misconfiguration checks based on Microsoft Secure Score and CIS Benchmarks
Findings and Remediation
The assessment reported no critical or high-risk vulnerabilities. A few low-risk findings included:
- Lack of HSTS headers, which could increase the chance of insecure connections in specific edge cases
- Presence of plaintext credentials in a development repository, which have since been removed
We remediated the identified low-risk issues based on the recommendations provided. These updates were applied internally.
Outcome
- All critical and high-severity issues were resolved within two weeks
- Platform passed internal security review and GDPR audit
- Enabled rollout to enterprise pilot customers with confidence
- Helped establish a formal vulnerability management processPassed third-party penetration test with no critical or high-severity findings
- Authentication, access control, and encryption validated as robust
- Azure environment aligned with Microsoft and CIS best practices
- Enabled enterprise rollout with security confidence
- Delivered a secure system while avoiding recurring costs of commercial vendor tools
Standards Followed
- OWASP Top 10
- Microsoft Security Best Practices
- CIS Benchmarks
Conclusion
By embedding security from the architecture phase and leveraging open standards and cloud-native controls, we delivered a production-ready, secure platform. Independent validation confirmed its resilience and demonstrated that strong security can coexist with cost efficiency.
